Yet another Drupal scanner – Drupwn
Hi everyone,
Today, I will introduce you to a new tool, developed for the sake of our penetration testing activities, named Drupwn which claims to provide a reliable and efficient way to perform enumerations on Drupal web applications.
Drupwn is a python script, following a modular architecture for maintenance and enhancement purposes, which allows enumerating various kind of information that could be valuable to any security assessment against such platform.
Architecture
Before diving into the main subject, let’s take a look on its architecture.
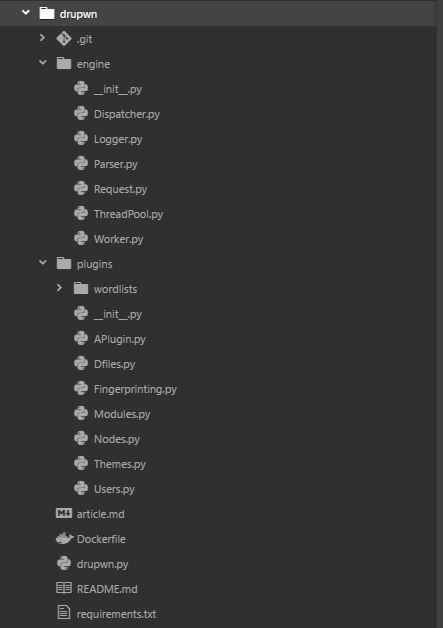
As you can see on the picture above, the engine and plugins parts are completely independent, allowing to easily add modules without having the modify the tool core engine.
Each plugin inherits from the abstract class APlugin, providing a better overall structure alongside the whole code base. Upstream the design concern, this inheritance provides a multi threading support by design, offloading the conundrum that is parallelization, to the core engine.
Each plugin is designed as follows :
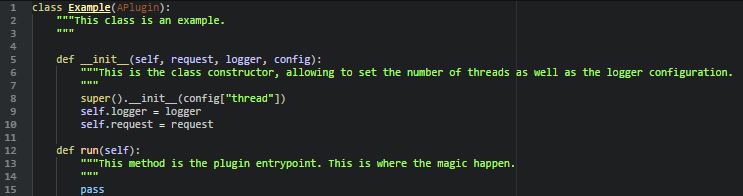
Once the plugin is created and added to the plugins folder, we must refer to it within the dispatcher and the parser in order to ensure its support by the reflective factory.
Quite easy right ? Thanks to this design pattern, anyone is able, within a few minutes, to add new functionalities to Drupwn!
Functionalities
To fit into as many situations as possible, Drupwn supports:
- Basic authentication
- Cookie manipulation
- User-Agent modification
- Logging
- Request sending speed
- Enumeration range customization
Upstream those passive functionalities, this python3 script actually provides 6 modules, described below.
User enumeration
As its name suggests, this module is used to enumerate the registered users on the platform assessed.
In fact, depending on the Drupal version, an unauthenticated user could be able to enumerate the existing users through the /user/{ID} resource.
Because code is more explicit than words, here is a piece of pseudo code, explaining the module inner working.
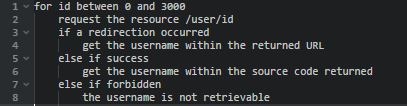
Node enumeration
When publishing an article, the CMS creates a node, associated with a slug. Lambda users use the slug name to access a given article. However, it is quite tedious to enumerate all the website’s pages using combinations of alphanumeric chars. Of course, spidering can be a good way to accomplish this job but, it is noisy as hell and a better solution exists.
Indeed, by iterating on the resource /node/{ID}, we can retrieve the associated slugs and map the whole website content. This can help find unlinked pages which can result to the gathering of sensitive information.
Default files enumeration
Well, this module just checks if the default installation files are present on the web server, helping improve server side hardening to reduce the attack surface.
Theme enumeration
Theme enumeration can seem useless however, some free themes available online can be backdoored, which is an easy win situation. This enumeration simply use a wordlist and print out the name of the installed themes.
Module enumeration
This module is very similar to the previous one nevertheless, we commonly encounter hardened installations, preventing any kind of module enumeration.
Modules are, 99 % of the time, the weak point of a Drupal application. This is why, finding a workaround is paramount to ensure the assessment reliability.
Here is how this plugin works:
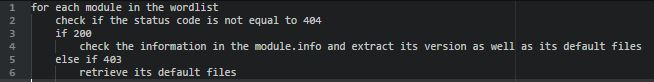
Fingerprinting
Fingerprinting a Drupal application can be quite difficult. Indeed, none of the CMS default files allows to efficiently determinate the version deployed. To remedy this situation, Drupwn uses several locations to accomplish this task.
Usage
Drupwn works out of the box thanks to its dockerization.
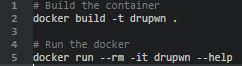
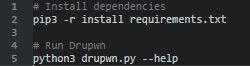
If docker seems unfriendly to you. Drupwn can be use directly on any system using pip3 and python3. To do so, follow the guidelines below:
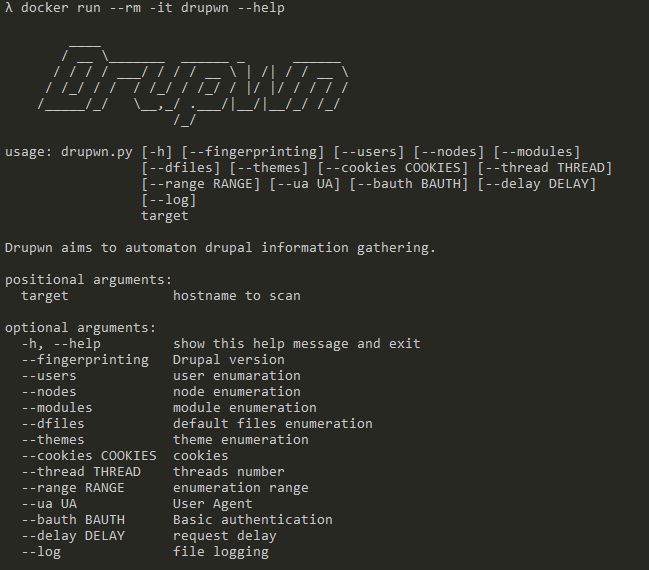
Examples
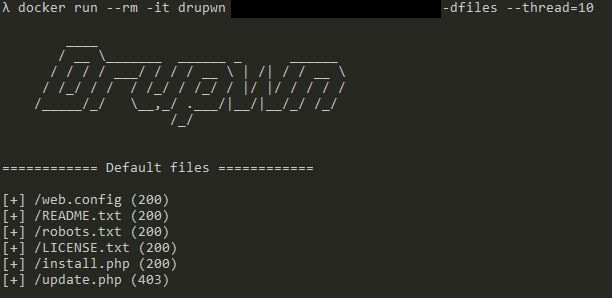
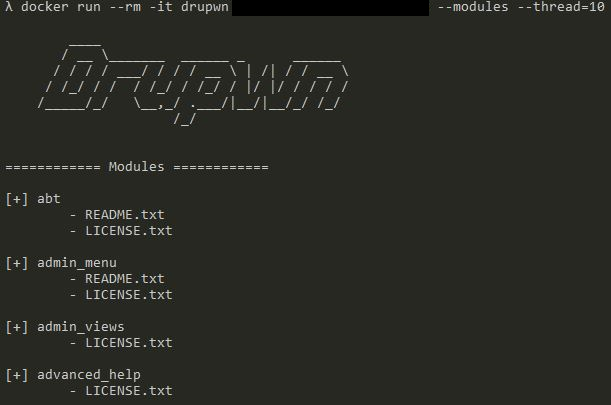
Conclusion
We believe our tool provides good capabilities of enumeration that can definitely help any pentester conduct, with efficiency and reliability, his security assessment.
As any open source project, pull requests are widely welcome! Here is a short list of desired features that will be implemented later:
- TOR network support
- Proxy support
- Vulnerability detection
Github repository => https://github.com/immunIT/drupwn
Happy hacking,
Jean Lejeune

Comments are closed.