XIP – IP addresses mutation
Hi everyone,
Today, I will introduce you to a new tool, developed for the sake of one of our pentesting engagement, named XIP.
XIP claims to provide an efficient way to generate a list of IP addresses, using a set of mutations, in order to bypass blacklists and security measures implemented to avoid hacker to pivot within a given a network.
As you probably already know, blacklist filtering is far from being reliable and there is always a way to circumvent it, which could lead to a full compromise of the information system targeted.
Let’s dive into the main subject by assuming the following scenario.
Let’s dive into the main subject by assuming the following scenario.
Scenario

As it can be seen on the picture above, the web application, accessible over the internet, requests the wanted server in order to provide data to the end user. A filtering process has been deployed on the web application, authorizing connections from the web application to a limited number of server, in this case the backend server.
Consequently, any connection attempt towards the other appliances will, undoubtfully, fail.
However, IP addresses can be interpreted by systems through different formats, allowing us to shunt the verification process and bypass the filtering system.
It is important to note that IP addresses are handled differently according to the operating system running on the underlying server. Consequently, it does not exist a universal escaping technique.
Nevertheless, having a large file of IP addresses mutated increase the success ratio :P. This is why XIP is born.
XIP tool
XIP provides several mutations and representations format. Below are the implemented transformations:
- Hexadecimal
- Decimal
- Octal
- IPV4 to IPV6 conversion
- Dotless
- Zeroless
- Padding
- Overflow
Moreover, these mutations can be performed randomly, allowing you to push the filtering system to its limits.
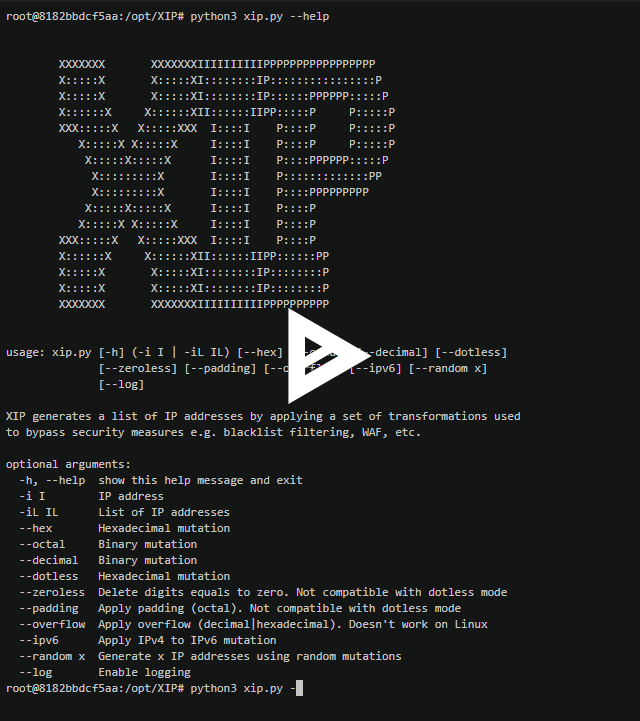
Usage
XIP works out of the box thanks to its dockerization
- Docker pull immunit/xip
- Docker run –rm -it immunit/xip –help
If docker seems unfriendly to you. , XIP can be directly used on any system using python3.
- Python3 xip.py –help
Example
Conclusion
Bypassing such filtering system often lead to critical discovery e.g. SSRF, RCE, etc. We believe that our tool could be, combined with the BurpSuite intruder, valuable to any security assessment.
As any open source project, pull requests are widely welcome!
Github repository => https://github.com/immunIT/XIP
Happy Hacking,
Jean


Les commentaires sont fermés.